AI-driven embedded IDPS for CAN, Ethernet and RF—built for the SDV lifecycle.
Secure Elements' embedded portfolio combines AI feature extraction, policy-driven prevention and AUTOSAR-aligned security events, aligned to ISO/SAE 21434 and UNECE R155. Every sensor is tightly linked to CRISKLE Workspace (TARA) and CRISKLE MSOC, giving your teams end-to-end visibility, evidence continuity, and lifecycle traceability.
Technical scope (embedded + operational)
Built for production-minded automotive programs: deterministic edge execution, structured security events, and governed operational response.
- Telemetry capture & feature extraction across CAN/CAN-FD frames, Ethernet flows, and RF interactions.
- Model + policy separation: policies are authored/validated via configurator and updated via OTA without reflashing ECU code.
- Evidence-grade logging: event IDs, severity, timestamps, optional context blobs, and optional signatures.
- Ops automation: correlation rules trigger alerts, PSIRT tickets, and playbooks (including OTA policy rollout).
Detections are mapped to threat scenarios in TARA, logs are produced as structured security events, and MSOC workflows trigger alerts, PSIRT tickets, and playbooks up to and including OTA policy updates for ECUs.
At a Glance

What Secure Elements delivers
Embedded intrusion detection is only valuable when it connects engineering intent to operational outcomes. We deliver ECU-grade sensors plus the tooling and workflows required to deploy, tune, monitor and govern them.
AI feature extraction at the edge
Telemetry and signals are converted into robust features suitable for detection and policy enforcement, designed for embedded constraints.
AUTOSAR-aligned security events
Detections produce structured events, suitable for correlation and evidence reducing vendor-specific log parsing and integration friction.
Closed-loop operations
CRISKLE MSOC correlates IDPS logs, triggers rules, opens PSIRT tickets, executes playbooks, and can drive OTA policy updates.
Embedded IDPS portfolio
AI-driven CAN IDPS, AI-driven ETH IDPS and RF IDPS engineered to integrate with real ECUs/gateways, trained with your DBC/ARXML and traces, and operationalised through CRISKLE Workspace (TARA) and CRISKLE MSOC.
AI-Driven CAN IDPS
Detects anomalous and policy-violating behaviour on CAN / CAN-FD using AI feature extraction and engineered constraints. Supports real-time detection and prevention paths, while generating structured security events suitable for traceability and audit evidence.
- Train with your DBC to align signals and expected behaviour.
- Deploy on gateway/ECU targets and validate under realistic bus load.
- Map detections to TARA for lifecycle traceability in CRISKLE Workspace.
Typical targets include gateway-class compute and automotive boards. Replace assets at any time to match your internal hardware references.
AI-Driven ETH IDPS
Designed for service-oriented and IP-based in-vehicle architectures. Extracts features across OSI layers to detect abnormal sessions, malformed traffic, suspicious service interactions and segmentation/firewall policy violations.
- Bring ARXML (services, interfaces, communication) to ground model features.
- Provide PCAP from representative traffic to train and tune.
- Define playbooks in CRISKLE MSOC aligned to your response policy.
ETH IDPS feature capture spans L1–L7. The OSI stack visual is intentionally colour‑tinted for readability and visual separation.
RF IDPS for keyless access attacks
Addresses keyfob-related attacks such as relay and replay-style behaviours by modelling RF interaction sequences and detecting suspicious deviations. Delivered as a deployable component suitable for integration into a Body Control Module (BCM) AUTOSAR stack.
- Observe and model behaviour to establish normal interaction envelopes.
- Generate structured events with optional timestamp/context/signature fields.
- Operationalise in MSOC with escalation paths and OTA policy updates.

Replace assets/rf-keyfob.svg with your preferred keyless/RF marketing visual.
AUTOSAR-aligned security events
Structured security events are the bridge between embedded detection and enterprise-grade response. Our sensors are designed to emit events that can be handled in AUTOSAR-style pipelines and consumed cleanly by CRISKLE MSOC for correlation and response.
Why format fidelity matters
In automotive programs, evidence and traceability are as important as detection. Consistent event structure supports auditability, incident reconstruction, and automation—without brittle, vendor-specific parsing.
- Correlation-ready fields (IDs, source, severity, timestamps).
- Context support when deeper investigation is needed.
- Optional signature for integrity and non-repudiation patterns.
- Direct ingestion into MSOC rules, alerts, PSIRT tickets and playbooks.
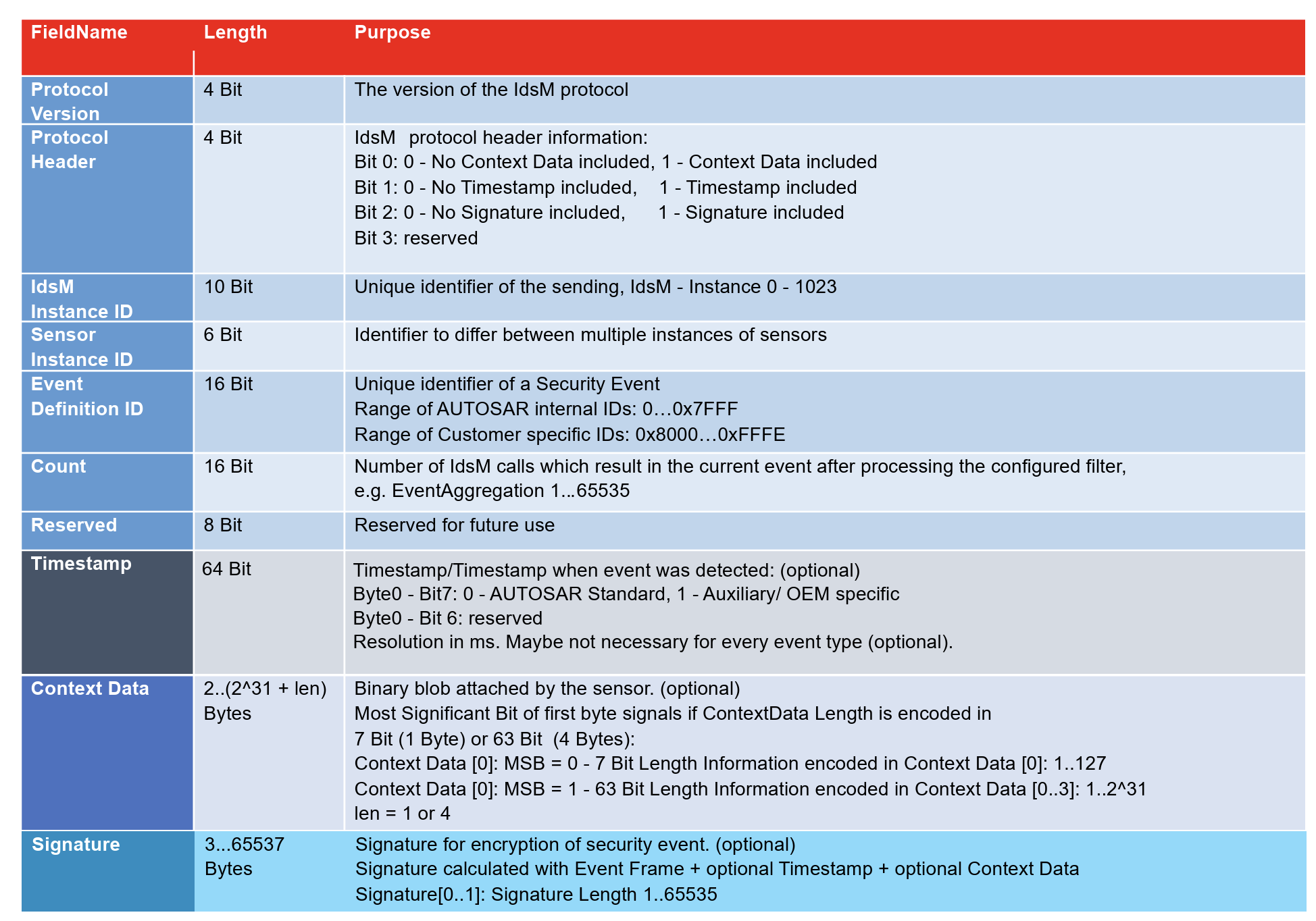
Protocol format: IdsM event frame fields and optional elements (timestamp/context/signature).
The same event definitions that drive embedded detections can be mapped back into CRISKLE Workspace (TARA) as mitigations and controls, ensuring a defensible thread from threat scenario → control → telemetry → response outcome.
End-to-End visibility: CRISKLE Workspace (TARA) → Embedded IDPS → CRISKLE MSOC
Replace spreadsheet-driven cybersecurity with traceable engineering artefacts and operational automation. Your teams get one coherent workspace from design-time risk to run-time response.
CRISKLE Workspace (TARA)
System specification and IDPS controls are mapped into TARA, preserving lifecycle traceability and enabling impact analysis as the architecture evolves.
- Threat scenarios, assets, interfaces and attack paths.
- Risk ratings and control intent (mitigations).
- Versioned linkage to IDPS policies and event definitions.
CRISKLE MSOC
Once IDPS logs and telemetry are sent, pre-defined rules and AI-assisted correlation trigger alerts, create PSIRT tickets, and run playbooks.
- Rule-based alerting with enrichment and severity.
- PSIRT case creation and audit-ready evidence.
- Playbooks including OTA policy updates for ECUs/gateways.
We integrate embedded telemetry, security-event formatting, policy lifecycle management and MSOC workflows so engineering teams can focus on product refinement, not multi-vendor plumbing.
Configurator-driven policies, updated by OTA
Each embedded IDPS includes a configurator to author and validate a policy file that can be updated over-the-air—supporting continuous improvement without destabilising ECU software.
Policy lifecycle, engineered
- Author policies for detection and prevention logic.
- Validate policies with guardrails and consistent schema.
- OTA updates to deploy new rules in response to emerging threats.
- Playbook linkage so each rule has an operational response path.
Typical training inputs include DBC, ARXML and representative traces (e.g., PCAP), enabling models to learn your real services, timing and traffic patterns.
Evaluate against your vehicle architecture
We can support a rapid technical workshop to place sensors in your architecture, define training inputs, and align TARA linkage and MSOC playbooks.
ECU/SoC constraints (CPU, RAM, scheduling), bus load and timing profiles, service/interface definitions (ARXML), representative traces (PCAP), AUTOSAR logging integration points, and your incident response policy (PSIRT escalation and playbooks).
Typical inputs
- DBC for CAN / CAN-FD signal mapping.
- ARXML for Ethernet services and interfaces.
- PCAP traces for training and validation.
- Cybersecurity policies for playbooks and escalation.
Outputs
- Policy files for each sensor + OTA update plan.
- TARA mapping and traceability in CRISKLE Workspace.
- MSOC rules, alerts, PSIRT ticketing and playbooks.
- Deployment guidance for ECU/gateway targets.
Industry Alliances & Strategic Partnerships
We collaborate with leading technology providers, research institutes, and mobility pioneers to advance the security of connected and autonomous vehicles.









Join Security Leaders. Stay Ahead.
Get insider updates and actionable insights from CRISKLE and our global partners—trusted by the world's mobility and security innovators.
Sign up for early access to feature rollouts, expert briefings, and key security alerts.
